How to fix Netapp expired self-signed certificate by creating a new one
Symptom: You are using ONTAP 9x (your Netapp is fairly new, within the last 4-5 years. These instructions probably don’t apply to old Netapp devices)
Symptom: When you look at the diagnostic logs on your Netapp, you get a warning that the certificates are expiring or expired:
Event:
mgmtgwd.certificate.expiring: A digital certificate with Fully Qualified Domain Name (FQDN) ExampleNetappServer1, Serial Number 569848B0A5092, Certificate Authority ‘ExampleNetappServer1’ and type server for Vserver ExampleNetappServer1 will expire in the next 29 day(s).
Message Name:
mgmtgwd.certificate.expiring
Description:
This message occurs when a digital certificate for a Vserver is about to expire. Client-server communication will not be secure if the certificate expires.
Action:
Install a new digital certificate on the system using the ‘security certificate create’ or ‘security certificate install’ command.
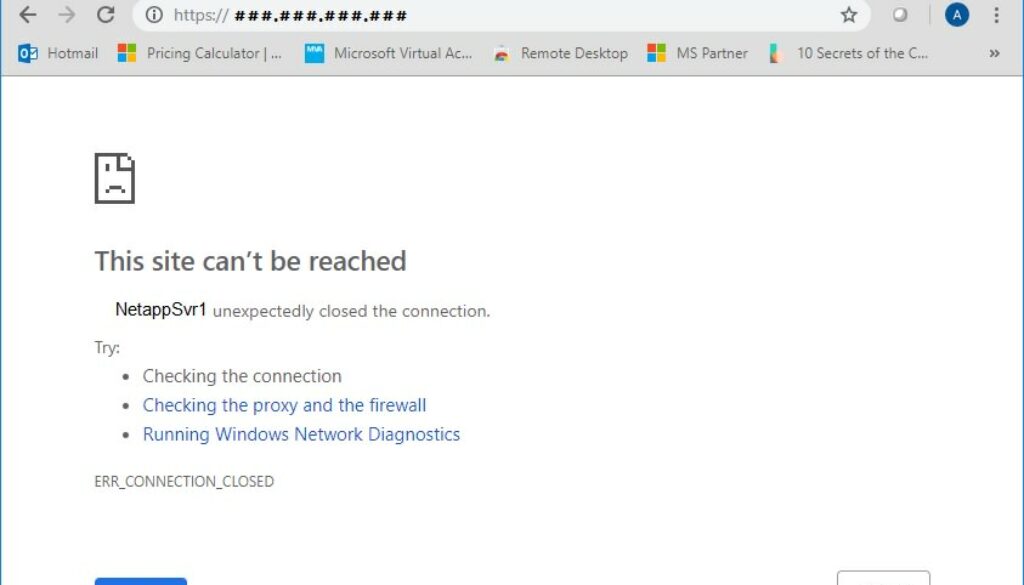
Symptom: When you try to reach the website for your Netapp OnTAP, it won’t connect at all.
See the image above for what this looks like.
Symptom: You tried to create new certificates using security certificate create and now the website is broken.
Whoops. Never fear, keep reading, this article will help you.
DIFFERENT ISSUE — Third Party CAs are expiring
Just recently (June-July 2019), ONTAP users are getting errors that several certificates of type “server-ca” are expiring. These are NOT the certificates you use for your Netapp website and the fix steps in this article do not apply to them.
CA certificate names expiring on July 09, 2019:
- DeutscheTelekomRootCA2
- UTN-USERFirst-Hardware
- Class2PrimaryCA
See my other article about how to fix expiring third party certificates ( type = server-ca ) if this describes your situation.
Solution
How can I connect if the Netapp website is down?
Use a terminal emulator such as Putty. Connect using SSH port 22, to the IP of your Netapp Cluster.
When prompted, type your administrator username and password. admin is the default username and netapp!123 is the default password.
Disclaimer: I’m just someone who admins Netapp SAN for my job. You should review the official Netapp articles on this topic and use common sense before making changes. If you aren’t sure about anything, put in a case with Netapp to get help.
Reference: Netapp KB article that describes how to renew the certificate with ssl modify.
First, capture your current status.
Here are the commands you will run to see the current status of your certificates:
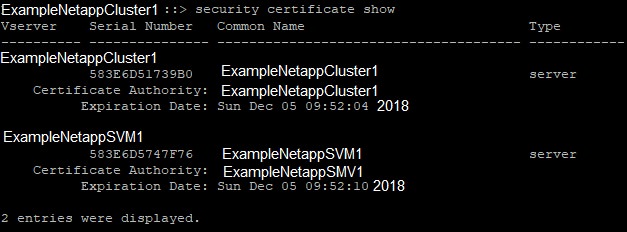
security certificate show
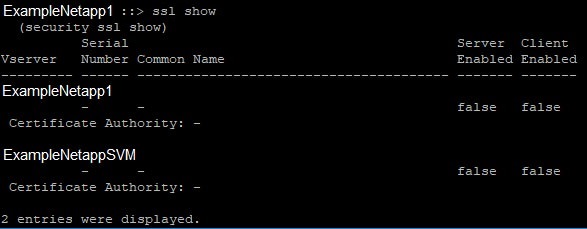
ssl show
Feel free to run these whenever needed, to see your status.
Run both commands now and screenshot or copy the results so you can reference them later.
Here is an example of a Netapp that has expired certificates for the cluster and the SVM:
Here is an example of a Netapp that has broken website ssl certificate:
.
Did you already delete your certificates and don’t know the names of your cluster and SVM?
Assuming you are connecting to your cluster, you should see the cluster name at the beginning of your command prompt.
If you press TAB while writing a command, Netapp will provide you possible answers. This can help you retrieve your Vserver list.
Type security certificate show -vserver [TAB]
Your command prompt will show you the possible answers. One should be your cluster, one should be your SVM(s).
Perform these steps to get rid of expired certificates, install new, and enable.
1. Delete old certificates:
Identify your variables:
-vserver = vserver name from the “security certificate show” command, such as ExampleNetappCluster1
-common-name = common name from the “security certificate show” command, such as ExampleNetappCluster1
-serial = serial number from the “security certificate show” command, such as 448293BA028
-type = type from the “security certificate show” command. Self-generated certificates are type server.
Run command for your cluster certificate: security certificate delete -vserver ExampleNetappCluster1 -serial ########## -type server -common-name ExampleNetappCluster1
When prompted, type Y to delete.
Run the command again for each SVM certificate: security certificate delete -vserver ExampleNetappSVM1 -serial ########## -type server -common-name ExampleNetappSVM1
When prompted, type Y to delete.
2. Create new self-signed certificates:
Run command for your new cluster certificate: security certificate create -vserver ExampleNetappCluster1 -common-name ExampleNetappCluster1 -type server -expire-days 999
You can change the expire-days per your security policy. The default is 365.
Run command for each new SVM certificate: security certificate create -vserver ExampleNetappSVM1 -common-name ExampleNetappSVM1 -type server -expire-days 999
3. Enable SSL with the new certificates:
Run command for your new cluster certificate: ssl modify -vserver ExampleNetappCluster1 -server-enabled true
Run command for each new SVM certificate: ssl modify -vserver ExampleNetappSVM1 -server-enabled true
4. At this point, your website should be back up!
Please leave comments if this worked for you, or tips if it didn’t.
If you need further reference, I found these Netapp articles helpful.
Reference: Netapp KB article that describes how to renew the certificate with ssl modify.
Selfish plug time (sorry!)
Thanks for reading this article! I hope it helps you! If you have tips or feedback, please comment or send me an email so that others can benefit.
I am a consultant in the Maryland/DC area in the USA. My specialties are Windows migrations (to 2016 and to Office 365 / Azure), VMware migrations, Netapp and SAN, and high availability / disaster recovery planning. If you would like help with your complex project, or would like a architectural review to improve your availability, please reach out! More information and contact can be found on the About page. – Amira Armond



August 7, 2019 @ 8:04 am
Hi Amira,
I’m experiencing more or less the same issue.
I migrating from one pair of node to another and my cluster management lif soon it is migrate return the same screenshot as yours.
If I move back all is ok. If I’m creating a new lif to this new pair of nodes, it doesn’t works.
If I disable http services I have an other message (not accessible 404)
So it is related to the new nodes
If I’m looking at the certificates, nothing is strange:
::> ssl show
(security ssl show)
Serial Server Client
Vserver Number Common Name Enabled Enabled
——— —— ————————————— ——- ——-
cluster
123A456ED7890
cluster true true
Certificate Authority: cluster
::> sec certificate show -serial 123A456ED7890
(security certificate show)
Vserver Serial Number Certificate Name Type
———- ————— ————————————– ————
cluster 123A456ED7890 cluster_123A456ED7890 server
Certificate Authority: cluster
Expiration Date: Wed Aug 28 14:42:37 2024
Do I still have to renew my certificate or you have another idea?
Thanks
August 9, 2019 @ 10:00 am
So I did a delete / renew of my current certificate, all goes well now.
January 7, 2020 @ 3:40 am
Hi,
Quick question, when I try the command to delete my certificate for both the cluster and SVM, I get an error: Either specify all keys, or set at least to “*”.
I am using the -serial switch to ensure I am deleting the correct certifiacte.
Cheers
Giles
January 7, 2020 @ 5:47 am
That message means you haven’t identified the certificate enough. Maybe there are two certs with the same serial? Seems unlikely but that is the thinking. Add more specifics about the cert (keep pressing tab on the command and see what netapp wants to add)
May 18, 2021 @ 6:08 am
pressing tab or write -ca
June 8, 2020 @ 11:39 am
thank you for the instructions. I’m new to NetApp and appreciate the guidance.
January 21, 2021 @ 8:07 pm
I have deleted few expired certificates and needed to create one again. These are of type server-ca, when tried to recreate it, it says “Command Failed: Cannot use certificate of type “Server-ca” for this operation.
Checked with Lenovo / Netapp support and they asked to upgrade OS and BMC version. This is what we are running now.
Lenovo Release 9.6P2: Fri Jul 19 02:10:57 EDT 2019
System ID: 0538123081 (XXXXXXXXXXXXX); partner ID: 0538123082 (XXXXXXXXXXXXX)
System Serial Number: 941936000292 (XXXXXXXXXXXXX)
Service Processor Status: Online
Firmware Version: 11.3P2
I tried to follow the above article , but clicking the hyperlink in the above article takes back to the same article.
Please help how can I create certificate of type server-ca